The Organization’s security program ensures compliance with a multitude of industry standards, regulations, and best practices through a single framework, based upon the Unified Compliance Framework (UCF), by aggregating authoritative sources into a collective whole. This framework then aligns and harmonizes the mandates within a de-duplicated list of common controls.
Internal Policies
As part of the Security Governance Framework, the Security team has adopted common definitions for policies and associated documentation. This hierarchy guides the structure of these documents to ensure consistent application throughout the Organization.
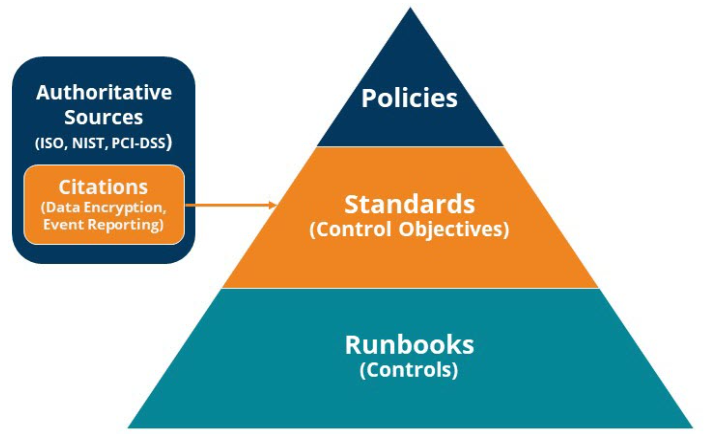
| Authoritative Sources EXAMPLE: ISO or NIST | Guidance, standards, requirements, and best practices to ensure confidentiality, integrity, and availability of information Shape and maintain effective information security practices |
| Citations EXAMPLE: ISO 6.8 – Information Security Event Reporting | – Specifications defined by authoritative sources to satisfy standards/control objectives and ensure protection of information, systems, and assets – Address potential risks and safeguard sensitive information and systems |
| Policies EXAMPLE: Zayo Security Policy | – Overview of corporate security standards/control objectives intended to guide decision making and operations – Long-term focus with routine reviews, but remain fairly static – Shaped by leading governance practices, laws, regulations, and industry standards |
| Standards (Control Objectives) EXAMPLE: Technical Security Standard | – Built from authoritative source citations to set parameters or configurations that support policy – Updated more frequently that Policies and span multiple topic areas – Multiple standards may be associated with a single policy – Multiple runbooks may be associated with a single standard |
| Runbooks (Controls) EXAMPLE: Secure Coding Runbook | – Procedures, plans, guidelines, or processes owned by different parts of the Organization and applied to entities/assets to satisfy standards/control objectives |
Zayo does not share internal governance documents in their entirety as they are treated as internal resources that are proprietary in nature. This fosters accountability and confidentiality, guiding teams through crises while ensuring compliance with industry standards. This approach underscores Zayo’s commitment to resilience and security. Tables of contents are available for download:
Security Governance Framework
Zayo Security Policy
Acquisition or Sale of Facilities, Technology, and Services Standard
Audits and Risk Management Standard
Harmonization Methods and Manual of Style Standard
Human Resources Management Standard
Leadership and High Level Objectives Standard
Monitoring and Measurement Standard
Operational and Systems Continuity Standard
Operational Management Standard
Physical and Environmental Protection Standard
Privacy Protection for Information and Data Standard
Records Management Standard
Systems Design, Build and Implementation Standard
Systems Hardening Through Configuration Management Standard
Technical Security Standard
Third Party and Supply Chain Oversight Standard
External Policies
Zayo is dedicated to conducting business with the highest level of integrity and responsibility. We believe that ethical practices and compliance with all relevant laws and regulations are fundamental to building trust and ensuring the long-term success of our relationships with customers, partners, and stakeholders.
We are committed to maintaining transparency, fairness, and accountability in all our business dealings, adhering to the highest ethical standards and continuously monitoring our operations to ensure compliance with applicable laws and industry regulations. Our external policies are available to all under the Governance category of Trust Center.