What is the difference between a risk and an issue?
A risk is a potential event or condition that, if it occurs, could impact Zayo’s ability to achieve its business objectives. A risk represents uncertainty about what may or may not happen in the future. A risk rarely goes away, but the level of risk may change based mitigation strategies to lower the impact to the business and likelihood of it occurring.
An issue is a current problem or situation that is affecting the Organization right now. It’s something that has already occurred or is currently happening and requires resolution.
Does collaboration exist between relevant related functions including Internal Audit, Information Technology, Security, Legal / Compliance, Risk Management, and Business Continuity to measure and manage cyber risks?
Yes, there is formal and consistent collaboration between functions. Zayo’s Risk Management program aligns with the Three Lines of Defense model, consisting of operational units (1st line), risk management and compliance functions (2nd line), and internal audit (3rd line). This multi-layered defense model enhances our ability to identify and address risks and promotes accountability, transparency, and resiliency across the Organization.
How is the senior cyber security leader engaged during reviews of strategic decisions including significant capital investment, new market entry, new product development, or M&A activity?
- Provides insight into risks before a decision is made
- Provides insight into risks after a decision has been made
- Assists in evaluating commercial impact to the business risk profile
- Provides recommendations for risk remediation strategies and action plans once a decision is made
How are risks identified?
The 1st line of defense, our operational managers and staff, is responsible for identifying risks and issues within their areas and ensuring that the processes and activities are controlled.
How are risks assessed?
The risk assessment process is coordinated by the 2nd line of defense, our Risk Management and Compliance teams. When a risk is identified by the 1st line of defense, the 2nd line ensures the risk is added to the Risk Register. The risk is then assigned to the appropriate 1st line operational unit, who then formally assesses the risk to determine a risk rating based on impact and likelihood.
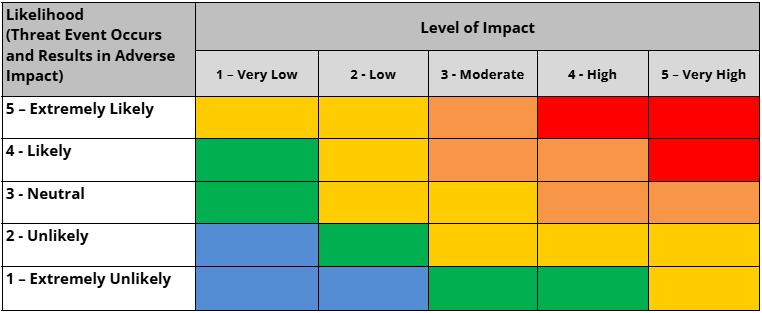
How are risks treated?
Once a risk has been identified and assessed, one or more risk treatment options is then applied to the risk:
| Treatment: Response from 1st line on how they will manage the risk | |
|---|---|
| Accept | Accept risk within risk tolerance levels without the need for additional action. Where the risk acceptance relates to non-compliance with a policy or standard, a policy exception is completed to document the risk acceptance. |
| Avoid | Apply responses to ensure that the risk does not occur. Avoiding a risk may be the best option if there is not a cost-effective method for reducing the risk to an acceptable level. The cost of lost opportunity associated with such a decision is considered as well. |
| Mitigate | Apply actions (controls) that reduce the threats, vulnerabilities, and impacts of a given risk to an acceptable level. Responses may include those that help prevent a loss or limit such a loss by decreasing the amount of damage and liability. |
| Transfer | For risks that fall outside of the tolerance levels, the level of risk may be reduced to an acceptable level by sharing a portion of the consequences with another party. While some of the financial consequences may be transferable, there are often consequences that cannot be transferred. |
Does Zayo have processes relating to remediation of security risks and vulnerabilities, and how does Zayo intend to use these processes to remediate any security-related issues discovered in relation to systems holding or processing customer data?
Processing and/or storage of personal data transferred by customers is limited to contact information (e.g., names, addresses, contact details, IP addresses) of customer employees, representatives, contractors or agents who are involved or interact with Zayo in the provision of services by Zayo to the customer under the agreement. Zayo is not the controller of customer data. The risk assessment process is coordinated by the Security Team, identification of threats and vulnerabilities is performed by asset owners, and assessment of consequences and likelihood is performed by risk owners. Risk treatment is implemented in response to each risk and is conducted by the teams relevant to the risk.